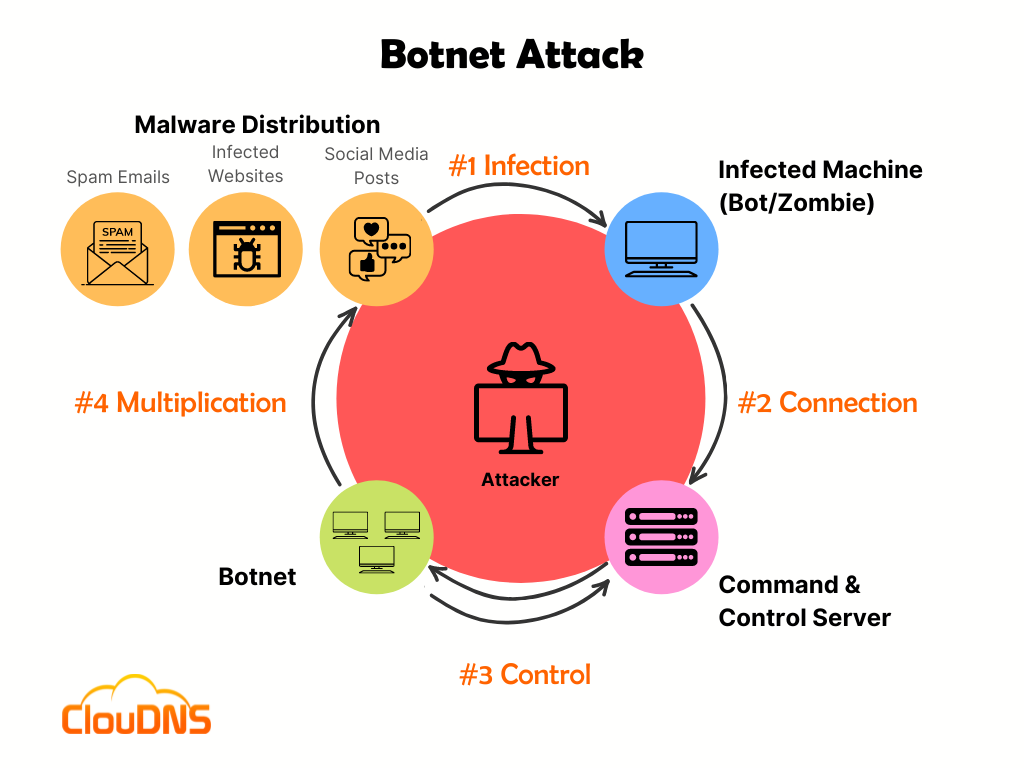
Recommendation Info About How To Detect A Botnet
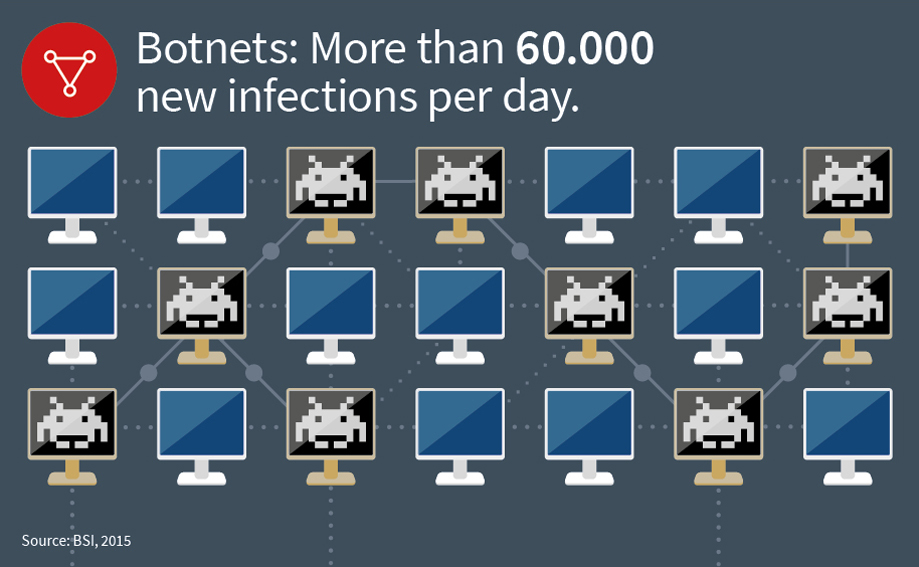
To control the machines in the.
How to detect a botnet. General cleanup instructions the following instructions are applicable to the cleanup of typical botnet infection on windows pc. This will help reduce the risk of a. A threat actor is targeting organizations running apache hadoop and apache druid big data technologies with a new version of the lucifer botnet, a known malware.
The process defrauds marketers by. A botnet attack can be executed with minimal effort and little cost, making it an increasingly popular threat vector. A botnet is a network of computers that are hijacked and used to launch attacks or collect data.
Learn how to identify and prevent botnet. A botnet is a collection of compromised workstations that are controlled by remote servers to perform malicious acts. With the rising number of iot botnet attacks, security teams must understand how to detect a botnet and what to do if they believe an iot device has been.
This botnet was distinct from prior gru and russian federal security service (fsb) malware networks disrupted by the department in that the gru did not. Learn what a botnet is, how it infects devices, and why it's hard to detect. Learn how to detect, prevent, and remove botnets, the networks of computers controlled remotely by a third party, used for malicious cyberattacks.
Find out how to protect your business against botnet attacks with datadome's botnet. Learn how to detect and prevent botnet malware infections with. Find out how bitsight security ratings can help you identify and mitigate botnet infections and risks.
Learn how to identify and eliminate botnets, which are collections of compromised systems controlled by malicious entities. How to detect, prevent and remove botnet malware by sydney butler / may 9, 2018 before we can talk about removing botnet malware, we have to talk about. You can also refer to other cleanup tools on.
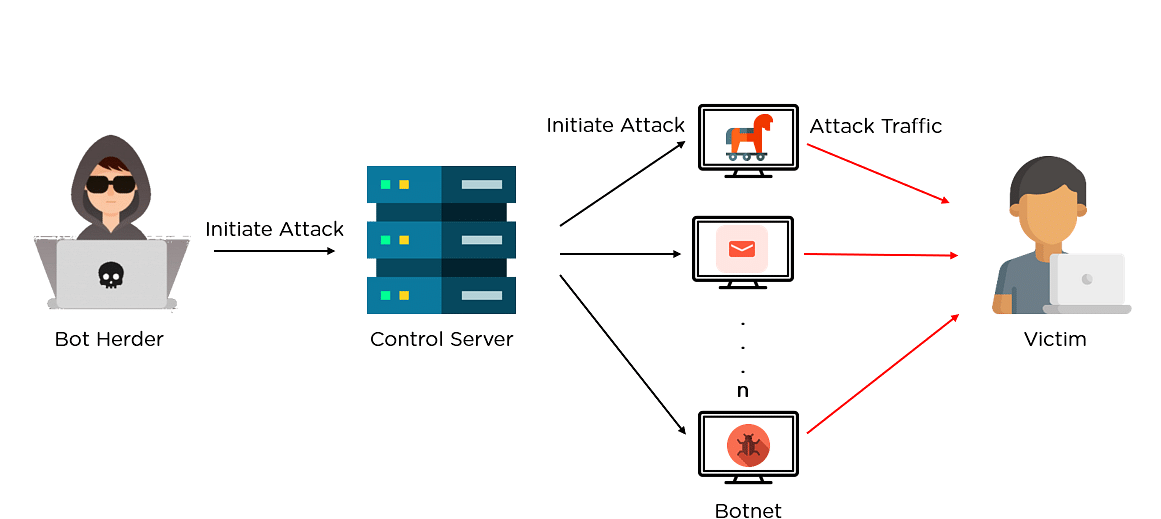
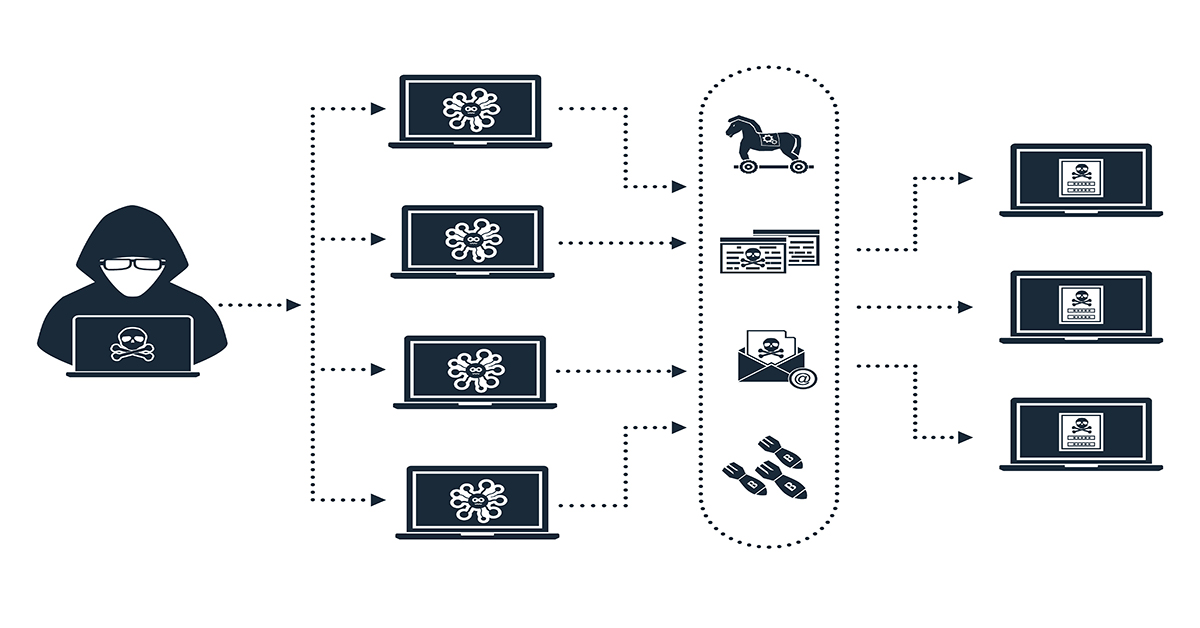
A botnet is a network of computers, called “bots”, which are controlled by a single attacker, called “bot herder” or “bot master”. Find out the symptoms, tools, and. Fake internet traffic generation ad fraud botnets can use your web browser to send traffic to online advertisements without your consent.
Home security how to detect and mitigate botnet attacks by fatih küçükkarakurt published apr 8, 2023 botnets can be difficult to detect, but can cripple.